Jenkins CI/CD Pipeline
Secure, automated DevSecOps pipeline for Spring Petclinic
Project Overview
Designed and implemented a complete Jenkins-based CI/CD pipeline for the Spring Petclinic application. The pipeline automates build, testing, security scanning, Docker image creation, artifact publishing, and notifications using DevSecOps best practices.
Pipeline Highlights
- Designed and implemented an end-to-end CI/CD pipeline using Jenkins for automated build, test, security scanning, and deployment.
- Integrated Maven-based build lifecycle with compilation, packaging, and artifact deployment to Nexus Repository.
- Performed static code quality analysis using SonarQube with enforced Quality Gates to ensure code reliability.
- Implemented filesystem vulnerability scanning using Trivy to detect security risks early in the pipeline.
- Integrated OWASP Dependency-Check to identify known vulnerabilities in third-party dependencies.
- Automated Docker image build and versioning using Jenkins build numbers for traceability.
- Pushed container images to both Docker Hub and Nexus Docker Registry for redundancy and artifact management.
- Implemented secure credential management using Jenkins Credentials for SonarQube, Docker, Nexus, AWS, and email notifications.
- Configured automated email notifications with build status, reports, and security scan artifacts.
- Installed and configured AWS CLI dynamically within the pipeline for cloud integration tasks.
- Automated application artifact upload to Amazon S3 for centralized storage and distribution.
- Adopted shift-left security practices by integrating security and quality checks early in the CI/CD lifecycle.
- Ensured pipeline resilience with timeout handling and build failure enforcement on quality gate violations.
- Built a fully auditable and repeatable delivery pipeline aligned with DevOps and CI/CD best practices.
Project Gallery
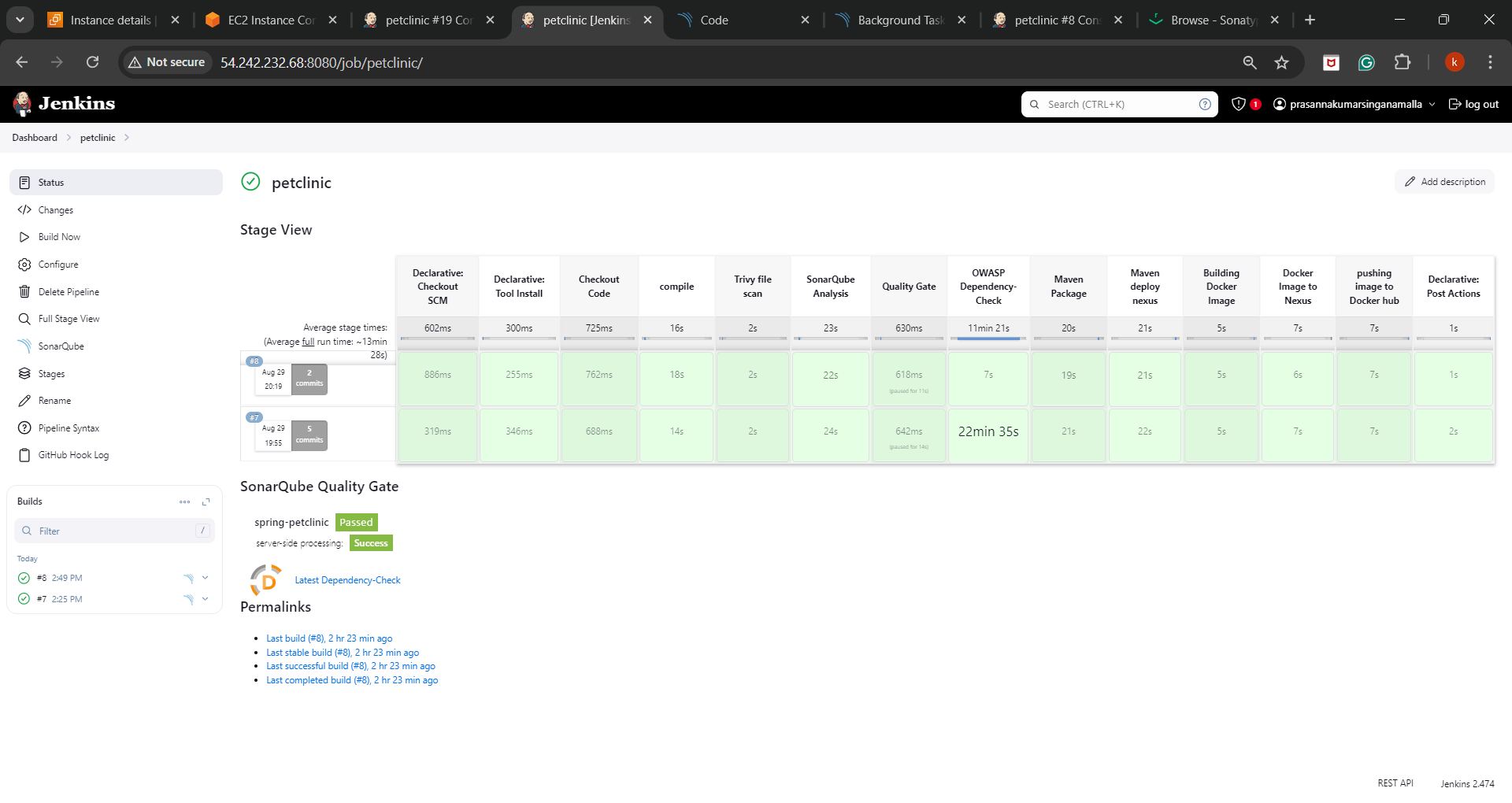 Pipeline Stages
Pipeline Stages
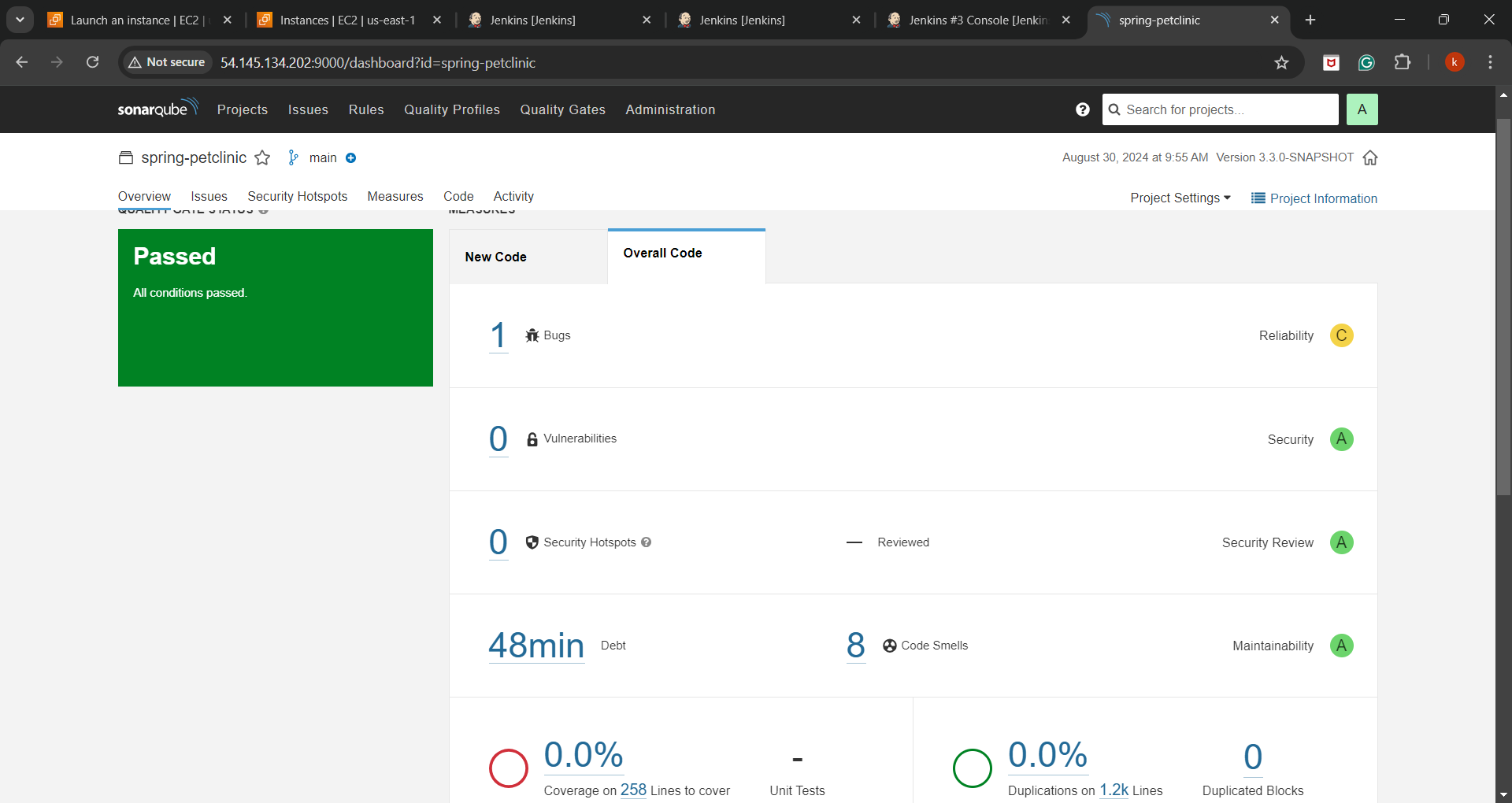 SonarQube Dashboard
SonarQube Dashboard
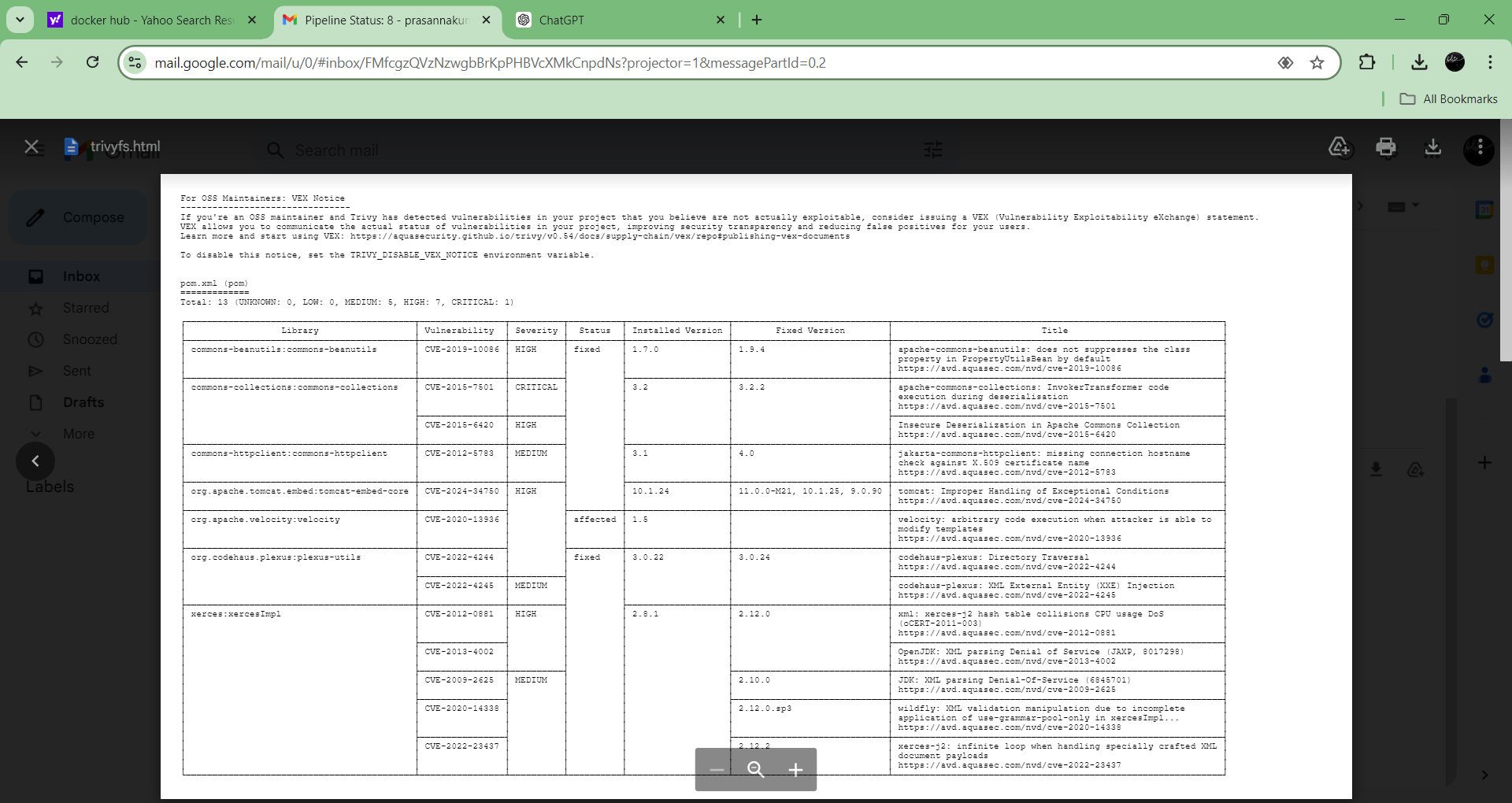 Trivy Scan Results
Trivy Scan Results
 Nexus Repository
Nexus Repository